The ABC's of Underwriting - Part 2
In the second of a two-part series, acquiring banks and payment service providers (PSPs) go back to school with Web Shield’s Andreas Stedry as he leads us through the alphabet of merchant underwriting.
Successful companies did not get to where they are today without taking risks. But it’s only those with robust risk management structures and confidence in them, who can be more enterprising and entrepreneurial. In short, take more calculated and controlled risks to boost their business, reputation, and bottom line. Underwriting is central to this.
N is for negative option billing.
Negative-option billing inverts the traditional sales process and assumes that the customer wants a good or service unless they specifically decline. By using pre-ticked boxes on the payment page, cardholders can be entered into ongoing subscriptions without their explicit permission.
Mastercard took aim at this form of deceptive marketing with a rule change in 2019. Merchants must now prominently provide the amount and date when the card will be charged, a convenient option to cancel subscriptions, trial periods that only begin the day products or services are received and written confirmation to the cardholder when the subscription is terminated.
Merchants with the MCC 5868 for Direct Marketing – Continuity/Subscription Merchants, are now classified as high-brand risk merchants and must be registered on Mastercard’s registration program.
O is for Opencorporates.
Opencorporates is a powerful, free, and publicly available open-source company database, which is especially useful during the pre-approval stage for an urgent merchant application. Depending on where your merchant is registered, you may be able to find basic as well as historical details on the company for due diligence purposes.
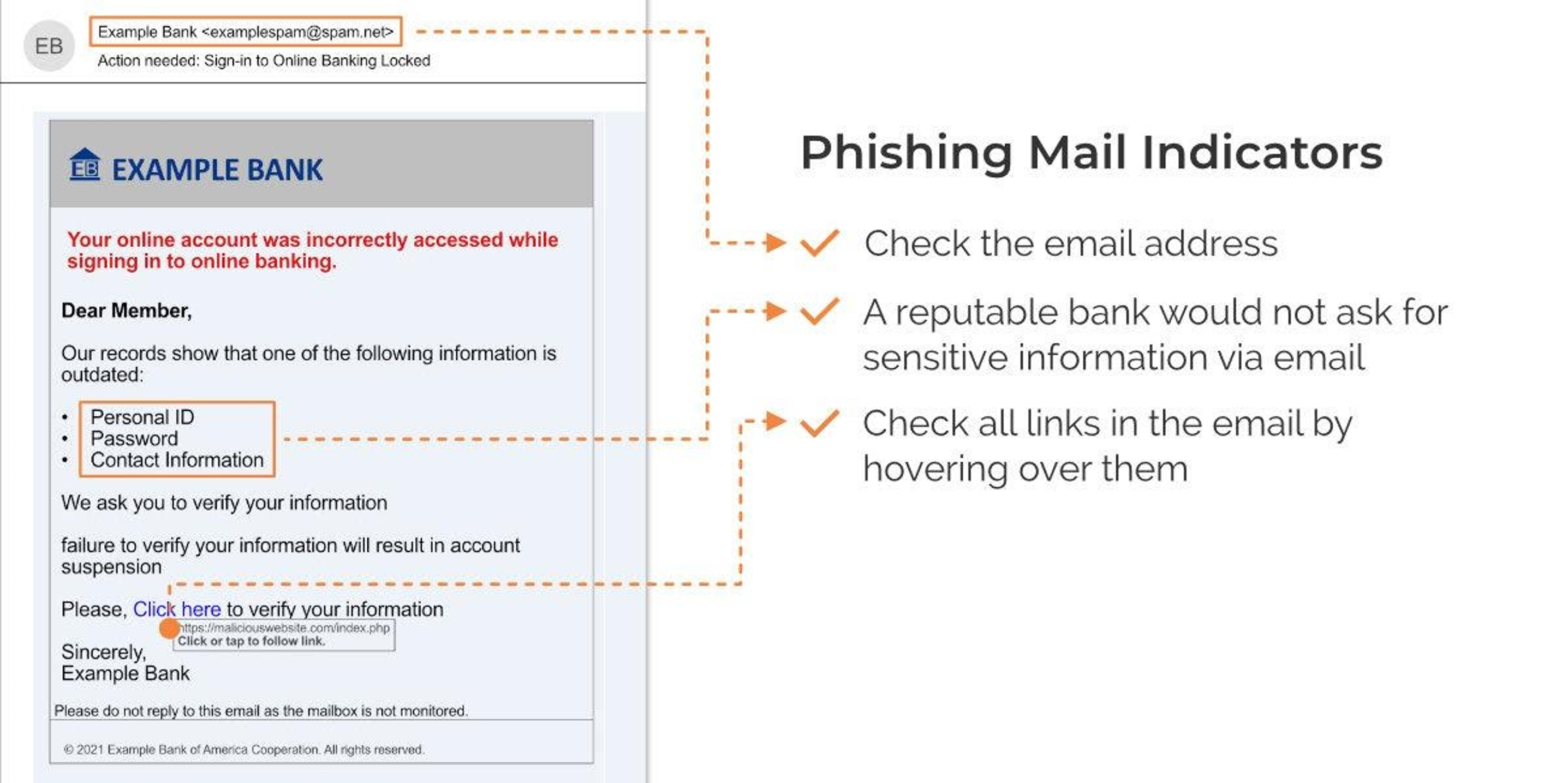
P is for phishing.
Phishing is a type of social engineering where an attacker sends a spoofed message designed to trick the victim into revealing sensitive information or deploying malicious software, such as ransomware.
E-mail phishing is most common, followed by voice phishing or vishing. This involves automated calls or real people calling under false pretenses to steal sensitive personal information, login credentials, or card data. Some tech support scams could be classified as a form of phishing.
Page phishing involves compromising legitimate web pages to redirect users to a malicious website, often a cloned site. Criminals sometimes simply copy the complete source code of one website and use it with only slight modifications. As merchant websites could be compromised, this is particularly relevant for underwriters.
Q is for QR code.
We’re all familiar with the two-dimensional barcodes which we can scan for more information or make a payment. But while QR codes often make our lives easier, we should also keep an eye on their potential for abuse.
That’s what happened to a Shanghai taxi driver when he parked in a restricted area. He returned to the car to find what he believed to be a ticket from the police with a QR code for payment. The profile picture of the receiving WeChat account showed a police officer. But it wasn’t a real ticket, and the money was sent to a private account.
R is for return fraud.
Return fraud is an online scam that occurs when someone purchases an item intending to return it immediately or uses duplicate receipts to get the money back. There are many variants, including ‘wardrobing’ – that’s buying something for a special occasion and returning it to the store when it’s no longer needed. Or using counterfeit receipts to request a refund from an online store for items that haven’t even been purchased. Or buying new products, replacing them with used or broken items, and returning the package to the seller. Afterward, the fraudster complains of having received damaged goods and requests a full refund.
S is for secure sockets layer or SSL.
SSL is a cryptographic protocol designed to keep information exchanged across a computer network secure. It’s used to protect personal data, login details, passwords, credit card, and banking details when they are transmitted online. As such, always make sure your merchants’ e-commerce pages are SSL secure.
T is for traffic analytics.
Reviewing the visitor traffic of a merchant’s website is often very useful for underwriters. There are several great providers in this area who nonetheless provide broadly the same types of metrics. First, the visitor count. Review the number of visitors to see how this has increased or decreased over a specific timeframe. These changes might have innocent explanations. Coinbase, for example, had more visitors during the crypto boom than now. But if you see sudden spikes in visitor numbers, this could indicate that the website is being used for load balancing or transaction laundering.
The traffic location shows you from where your merchant website is accessed. Imagine you’re about to onboard a gambling merchant from the UK with a UK gambling license. While reviewing the traffic you notice that almost 100% of the visitors come from Turkey where online gambling is forbidden. This is a clear red flag.
Also look at traffic sources to find out whether this is generated directly or via a referral link, by way of a search engine, social media, or an email marketing campaign. Consider all this information with what you know about the merchant’s business model to decide whether the merchant’s traffic is genuine and justifies their sales projections and average transaction values.
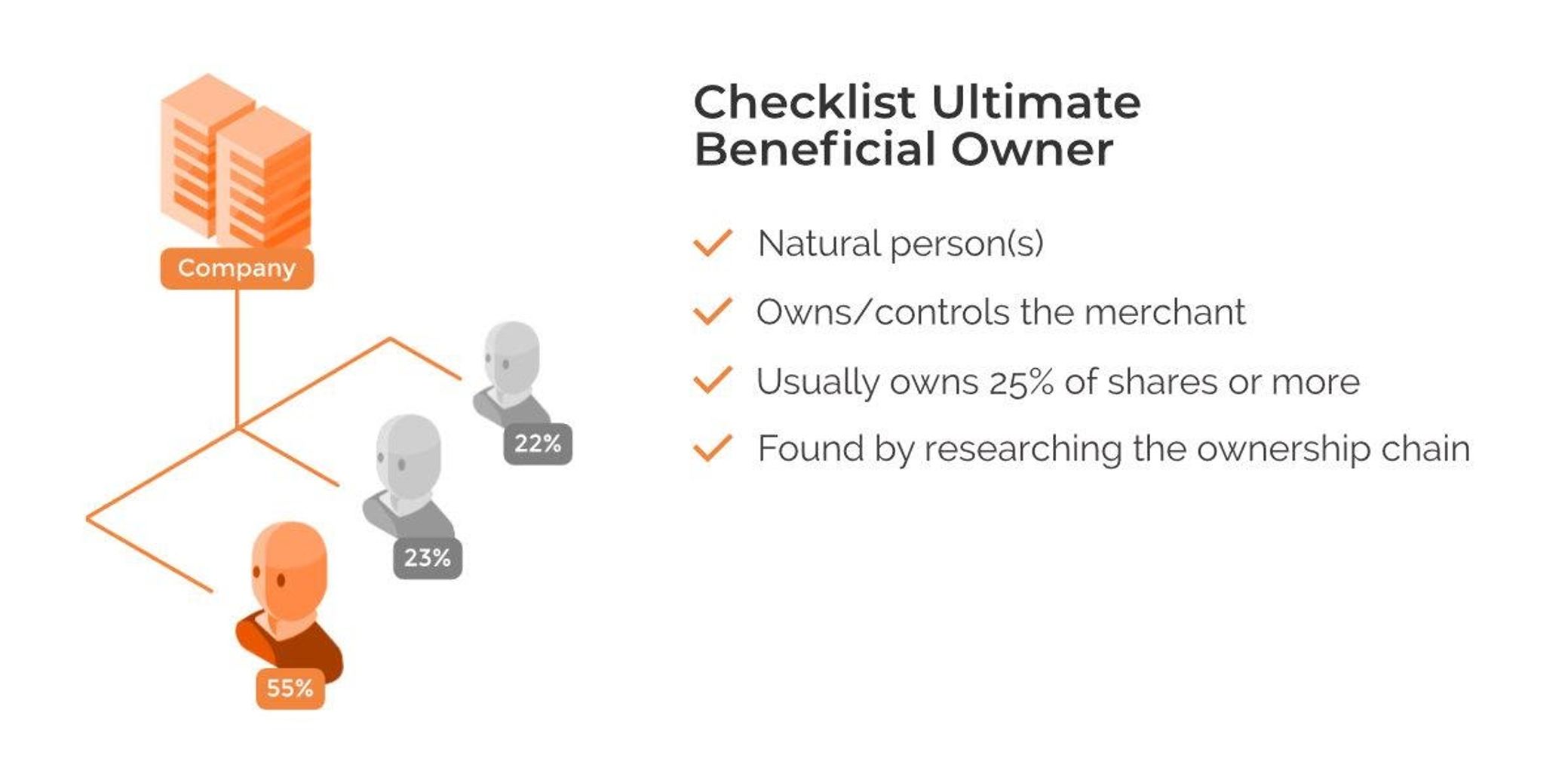
U is for the ultimate beneficial owner, or UBO for short.
The ultimate beneficial owner of a company is the natural person who ultimately owns or controls a merchant and/or the natural person on whose behalf a transaction is being conducted. It also includes those persons who exercise ultimate effective control over a legal person or arrangement. Usually, there’s a 25% threshold for company ownership, but this varies by jurisdiction.
In general, research the entity’s entire ownership chain until you have proof of ultimate ownership. Larger companies may have complex structures which are hard to break down. In the case of small e-commerce merchants, a complex ownership structure may be a red flag in itself, as it may be designed to conceal beneficial ownership. In this context, sanctions and PEP list screenings are essential.
V is for violations.
Content violations can be as ‘simple’ as an illegal ingredient in a nutraceutical product that you were unaware of, or an innocuous-looking Disney product for which the merchant isn’t licensed to sell. Other content violations are more challenging to detect and harder to deal with.
Take adult content merchants. They can offer free, paid, or subscription content, where illegal content may be hidden behind a paywall. Obtain login details for any closed or restricted areas from your merchant, but conduct your own mystery shopping, too. Unscrupulous merchants may set up fake ‘member areas’ with clean content while the questionable content is still active in a hidden, real member area.
Dealing with violations can be as straightforward as asking the merchant to remove the product in question. However, when it comes to more egregious breaches like the open sale of counterfeit luxury items or drugs, the only correct approach is to decline the merchant application or terminate the merchant account.
W is for Whois.
Looking up domain registrants via Whois has been an essential step in underwriting since the advent of e-commerce. Recent privacy regulations in the European Union have somewhat changed that. Much of the Whois information is no longer publicly available. Some merchants, especially in high-brand risk areas, are also using privacy services, who register the website on your behalf, concealing the name of their client.
Some of these hurdles can be overcome by using reverse Whois, where you work back from an individual to their registered domains. Or a historical Whois lookup tool, which shows past registrants of a domain.
X … doesn’t exist.
When underwriting, watch out for e-commerce merchants without a website. Legitimate businesses do not seek anonymity. They want to be known, recognized, and recommended. Having no web presence at all and no social media presence, including professional networks such as LinkedIn, is unusual. It also makes it impossible for underwriters to find content violations or other red flags.
Y is for… you!
As an underwriter, it’s your responsibility to construct the most accurate picture of a merchant possible to help inform the final decision to either approve or decline an application.
Sometimes you look at a merchant and have a bad gut feeling right away. If you are an experienced underwriter, you should trust yourself. Don’t forget to substantiate your suspicions with evidence, though. It’s about finding the sweet spot between trusting your professional experience and going into an investigation unbiased.
Consider your approach and ask the right questions. Oftentimes, it can be helpful to be straightforward. In other cases, it may make sense to ask open questions, where you already know the answers to see whether the merchant is honest or hiding something. Think of yourself as a detective working a case: gather the evidence, interrogate the suspects, and draw your final conclusions.
Z is for puzzle.
Underwriting and merchant due diligence is a kind of puzzle made up of different pieces.
Firstly, the corporate documents, which provide the basic details and start point for your investigation. After you have a solid foundation of data, it’s time to investigate this and then evaluate your findings. What needs further investigation? How should you address the merchant?
Next, calculate your risk. What risk areas did your findings address? How serious are the associated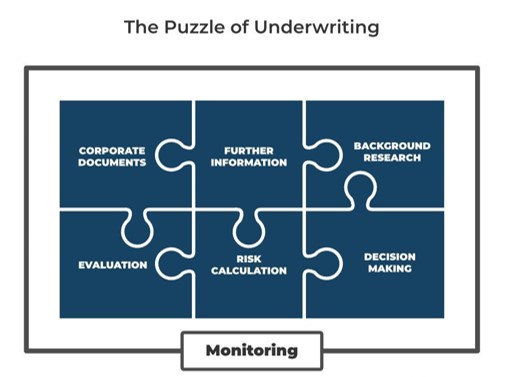 risks? Can they be mitigated? All these questions will lead you to the penultimate piece of the puzzle: making a decision of whether to board the merchant. The final piece of the puzzle is, of course, monitoring. Only through regularly re-underwriting and re-evaluating a merchant can we secure long-term compliance.
risks? Can they be mitigated? All these questions will lead you to the penultimate piece of the puzzle: making a decision of whether to board the merchant. The final piece of the puzzle is, of course, monitoring. Only through regularly re-underwriting and re-evaluating a merchant can we secure long-term compliance.
That brings us to the end of the ‘ABC of Underwriting’. It wasn’t an exhaustive list of everything an underwriter needs to know, but I think it illustrates rather convincingly that our work is sometimes surprisingly multifaceted.
Click here for the first part of the ‘ABC of Underwriting’.
About Web Shield
Web Shield – a ZignSec company, has been equipping the payments industry with tools to protect businesses from merchants involved in illegal or non-compliant activities since 2010. Our highly precise solutions enable acquirers, PSPs, and other financial organizations to evaluate new merchants and monitor existing ones, thereby saving both time and money.
Web Shield also organizes RiskConnect, a networking conference for risk management professionals. Delegates can access hours of great keynotes, presentations, and panels featuring industry experts online for free from 26 October 2021 and 12 months thereafter. Registration is now open.
SPONSOR DISCLOSURE: MAC is an independent, sponsor-supported membership organization. MAC has relationships with multiple card brands and industry vendors, but those relationships do not span the universe of possible solution providers within the industry. The article that appears in this blog post is from an organization from which MAC receives financial support. This blog post does not represent an endorsement by MAC of a product or service. Outside of defined sponsorship activities, MAC requests that content for our blog be educational in nature, but acknowledges that on occasion some educational content may also contain promotional material.

